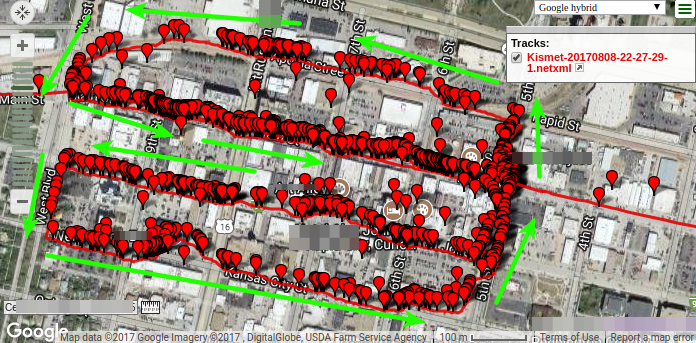
Gathering Proximity Card Credentials: The Wiegotcha

David Fletcher// There are a number of items that I watch on eBay. Included in that group are long-range proximity card readers. As it turns out, I was recently able […]
The post Gathering Proximity Card Credentials: The Wiegotcha appeared first on Black Hills Information Security, Inc..