Reading view
Offline Memory Forensics With Volatility

Volatility is a memory forensics tool that can pull SAM hashes from a vmem file. These hashes can be used to escalate from a local user or no user to a domain user leading to further compromise.
The post Offline Memory Forensics With Volatility appeared first on Black Hills Information Security, Inc..
WEBCAST: Windows Memory Forensics
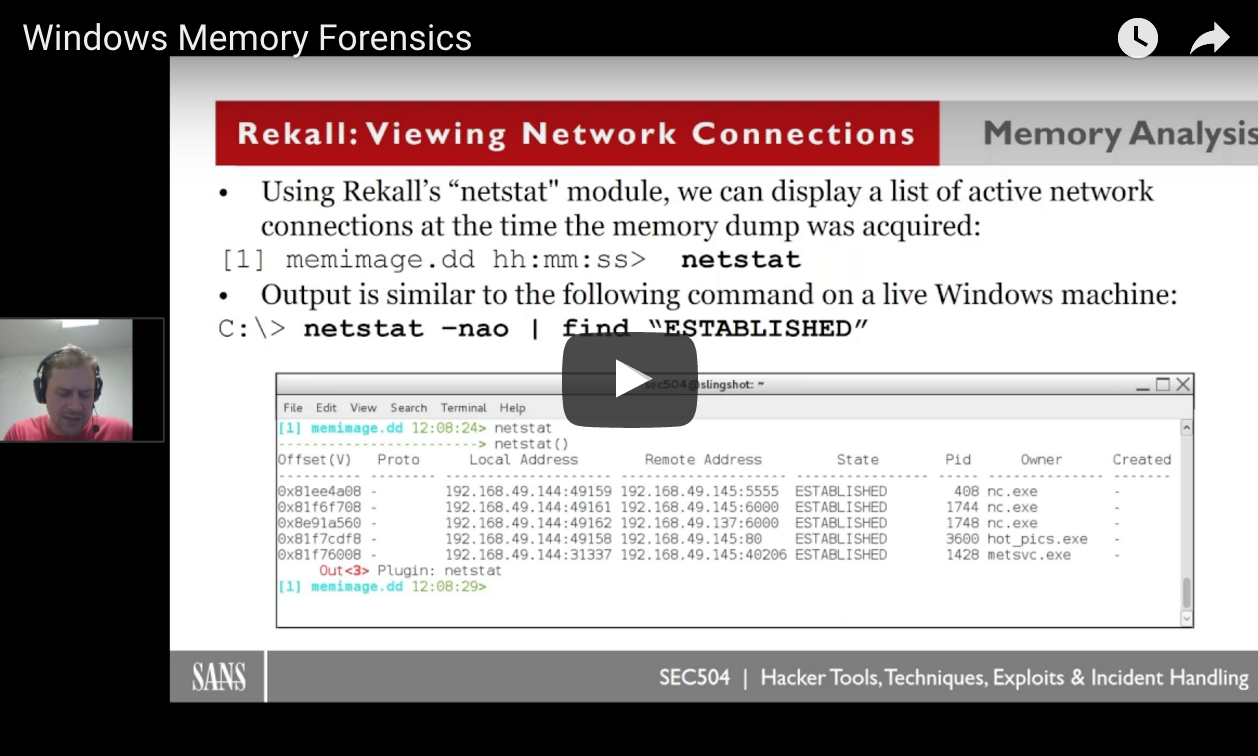
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]
The post WEBCAST: Windows Memory Forensics appeared first on Black Hills Information Security, Inc..
WEBCAST: Live Forensics & Memory Analysis
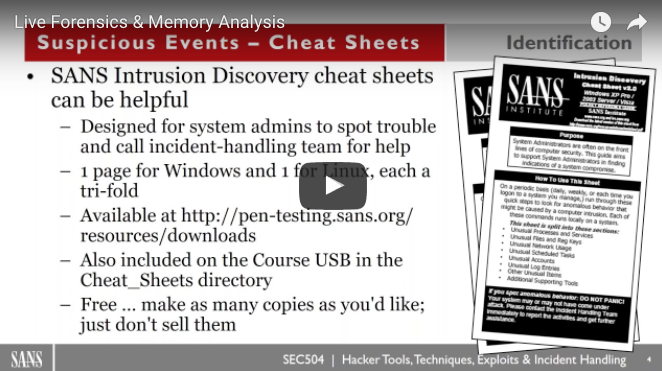
John Strand // So you think you might have a compromised Windows system. If you do, where do you start? How would you review the memory of that system? What […]
The post WEBCAST: Live Forensics & Memory Analysis appeared first on Black Hills Information Security, Inc..