WifiForge – WiFi Exploitation for the Classroom

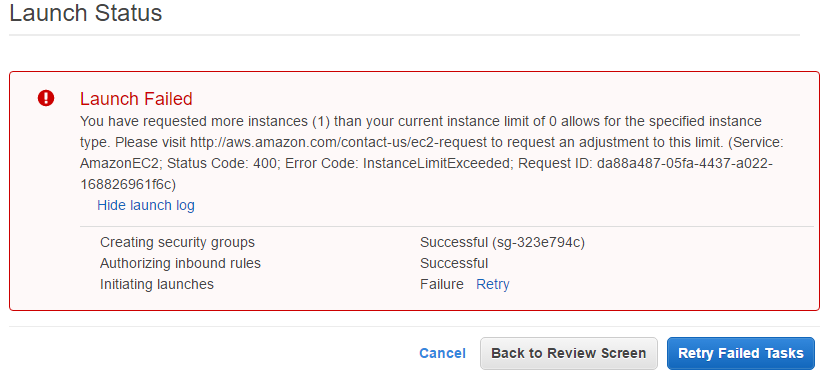
by William Oldert // BHIS Intern BHIS had a problem. We needed an environment for students to learn WiFi hacking safely. Our original solution used interconnected physical network gear […]
The post WifiForge – WiFi Exploitation for the Classroom appeared first on Black Hills Information Security, Inc..